Hackers caught taking over honeypot water pumping station
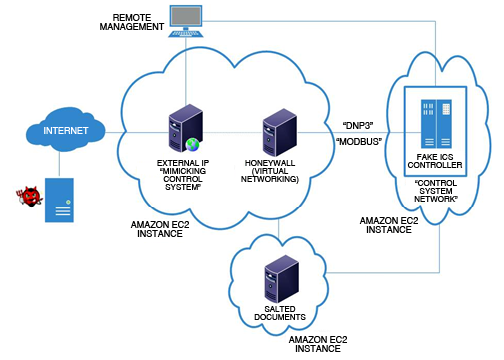
During the blackhat europe 2013 convention, Kyle Wilhoit of Trend Micro gave a talk about “Who’s Really Attacking Your ICS Devices?“. Kyle has set up a test decoy web server which mimics the operation of control station for water pumps.
According to the report (pdf file) it took only 18 hours for the first attack to start:
It took only 18 hours to find the first signs of attack on one of the honeypots. While the honeypots ran and continued to collect attack statistics, the findings concerning the deployments proved disturbing. The statistics of this report contain data for 28 days with a total of 39 attacks from 11 different countries. Out of these 25 attacks, 12 were unique and could be classified as “targeted” while 13 were repeated by several of the same actors over a period of several days and could be considered “targeted” and/or “automated.” All of these attacks were prefaced by port scans performed by the same IP address or an IP address in the same /27 netblock. In sum, China accounted for the majority of the attack attempts at 35%, followed by the United States at 19% and Lao at 12%.
The attacks aimed to modify Modbus traffic, modify CPU fan speed (which mimics the pump speed), access information and diagnostics pages and malware exploitation (including via email phishing).
Kyle recommendations are:
- Disable Internet access to your trusted resources, where possible.
- Make sure your trusted resources have the latest patches and that you diligently monitor when new patches/fixes are released.
- Use real-time anti-malware protection and real-time network scanning locally on trusted hosts and where applicable. (Some PLC systems cannot support anti-malware products because of the fragile nature of ICS protocols.)
- Require user name/password combinations for all systems, including those that are not deemed “trustworthy.”
- Set appropriately secure login credentials. Do not rely on defaults.
- Implement two-factor authentication on all trusted systems for any user account.
- Disable remote protocols that are insecure like Telnet.
- Disable all protocols that communicate inbound to your trusted resources but are not critical to business functionality.
- Control contractor access. Many ICS/SCADA networks utilize remote contractors, and controlling how they access trusted resources is imperative.
- Utilize SSL/TLS for all communications to web-based ICS/SCADA systems.
- Utilize network segmentation to secure resources like VES systems, ICS, and SCADA devices.
- Control access to trusted devices. For instance, for access to a segmented network, use a bastion host with access control lists (ACLs) for ingress/egress access.
- Improve logging in on trusted environments in addition to passing logs to SIEM devices for third-party backup/analysis.
- Develop a threat modeling system for your organization. Understand who’s attacking you and why.
The White paper, presentation slides and video are available here.
Hat tip Eyal Sela
Leave a Reply